Best SSH IoT Remotely: Your Ultimate Guide To Secure Connections
Ever wondered how you can securely connect to your IoT devices from anywhere in the world? The best SSH IoT remotely setup is your answer! In today's hyper-connected world, having remote access to your smart devices isn’t just a luxury—it's a necessity. Whether you're managing home security systems, monitoring industrial sensors, or controlling smart lighting, SSH offers a robust solution for secure communication. But here's the deal—choosing the right setup can be overwhelming, especially with so many options out there.
SSH, or Secure Shell, is like the secret agent of remote connections. It encrypts your data and ensures that your IoT devices stay protected from prying eyes. But what makes one SSH setup better than another? How do you ensure that your connection remains stable and secure no matter where you are? In this guide, we’ll break it all down for you, step by step, so you can make the best decision for your needs.
By the end of this article, you’ll know exactly how to set up the best SSH IoT remotely solution for your devices. So buckle up, because we’re diving deep into the world of secure connections, and you’re about to become a pro at it!
- Ullu Movierulz 2025 Telugu Download Your Ultimate Guide To Streaming And Downloading
- Unveiling The Secrets Of Moviesda 2023 Download Your Ultimate Guide
Table of Contents
- What is SSH?
- Why Use SSH for IoT?
- Choosing the Right SSH Setup
- Setting Up SSH for IoT Devices
- Securing Your SSH Connection
- Troubleshooting Common SSH Issues
- Performance Tips for SSH IoT
- Alternatives to SSH for IoT
- Real-World Examples of SSH IoT
- Conclusion: Your Next Steps
What is SSH?
Alright, let’s start with the basics. SSH, or Secure Shell, is like the superhero of remote connections. It’s a protocol that lets you securely access and control devices from anywhere, as long as you have an internet connection. Think of it as a secure tunnel between your device and the IoT system you want to manage. No hackers, no snooping—just you and your devices having a private chat.
SSH isn’t new—it’s been around since the ‘90s—but its importance has grown exponentially with the rise of IoT. Whether you’re controlling a smart thermostat from your phone or monitoring industrial equipment from halfway across the globe, SSH ensures that your data stays safe and your commands are executed flawlessly.
How Does SSH Work?
Here’s the deal: SSH uses encryption to create a secure connection between your device and the server. When you log in, SSH authenticates your identity using either a password or a key. Once you’re in, all communication between you and the server is encrypted, making it nearly impossible for anyone to intercept your data.
- Movie Rulz 2022 Your Ultimate Guide To The Best Films Of The Year
- Movie Hub Your Ultimate Destination For All Things Cinema
So, why is this important for IoT? Well, IoT devices often operate on open networks, which makes them vulnerable to attacks. SSH adds an extra layer of security, ensuring that your devices stay protected even in the most hostile environments.
Why Use SSH for IoT?
Now that we’ve covered what SSH is, let’s talk about why it’s the best choice for managing IoT devices remotely. Here are a few reasons:
- Security: SSH encrypts all data transmitted between your device and the IoT system, keeping it safe from hackers and cybercriminals.
- Reliability: SSH connections are stable and reliable, even over long distances or unstable networks.
- Flexibility: You can use SSH to manage a wide range of IoT devices, from smart home gadgets to industrial sensors.
- Scalability: Whether you’re managing a single device or an entire network, SSH can handle it all.
But here’s the kicker: not all SSH setups are created equal. To get the most out of your IoT devices, you need to choose the right setup—one that’s tailored to your specific needs.
Choosing the Right SSH Setup
So, how do you choose the best SSH setup for your IoT devices? Here are a few factors to consider:
Device Compatibility
First things first: make sure your IoT devices support SSH. Most modern devices do, but it’s always a good idea to double-check. Look for devices that come with built-in SSH support or can be easily configured to work with SSH.
Network Configuration
Your network setup can make or break your SSH experience. If you’re using a home network, make sure your router supports port forwarding and has a static IP address. For enterprise networks, consider using a dedicated SSH server to manage all your IoT devices.
Authentication Method
When it comes to SSH, there are two main authentication methods: password-based and key-based. Password-based authentication is simpler, but key-based authentication is more secure. If security is your top priority, go with key-based authentication.
Setting Up SSH for IoT Devices
Ready to set up SSH for your IoT devices? Here’s a step-by-step guide to get you started:
Step 1: Enable SSH on Your Device
Most IoT devices have SSH disabled by default. To enable it, log in to your device’s settings and look for the SSH option. Once you’ve enabled it, make sure to set a strong password or generate a key pair for authentication.
Step 2: Configure Your Network
If you’re connecting to your IoT devices from outside your local network, you’ll need to configure port forwarding on your router. This allows external devices to connect to your IoT devices securely. Make sure to use a strong firewall to protect your network from unauthorized access.
Step 3: Test Your Connection
Once everything is set up, test your connection by logging in to your IoT device from a remote location. If everything works as expected, congratulations—you’ve successfully set up SSH for your IoT devices!
Securing Your SSH Connection
Now that you’ve set up SSH, it’s time to make sure your connection is as secure as possible. Here are a few tips:
- Use Strong Passwords: If you’re using password-based authentication, make sure your passwords are strong and unique.
- Enable Key-Based Authentication: For added security, switch to key-based authentication and disable password login.
- Limit Access: Restrict SSH access to specific IP addresses or networks to reduce the risk of unauthorized access.
- Keep Software Up to Date: Regularly update your SSH software and firmware to patch any security vulnerabilities.
By following these tips, you can ensure that your SSH connections remain secure and protected from cyber threats.
Troubleshooting Common SSH Issues
Even the best SSH setups can run into problems from time to time. Here are a few common issues and how to fix them:
Connection Refused
If you’re getting a "connection refused" error, check the following:
- Make sure SSH is enabled on your device.
- Verify that port forwarding is correctly configured on your router.
- Ensure that your firewall isn’t blocking the SSH port.
Authentication Failed
If you’re having trouble authenticating, try the following:
- Double-check your password or key pair.
- Make sure your SSH client is configured correctly.
- Check the permissions on your SSH keys.
Performance Tips for SSH IoT
Want to get the most out of your SSH IoT setup? Here are a few tips to improve performance:
- Compress Data: Enable data compression in your SSH client to reduce bandwidth usage.
- Use a Faster Cipher: Choose a faster cipher algorithm to speed up your connection.
- Optimize Your Network: Make sure your network is optimized for low latency and high throughput.
By following these tips, you can ensure that your SSH connections are fast and reliable, even over long distances.
Alternatives to SSH for IoT
While SSH is the gold standard for secure remote connections, there are other options worth considering:
- VPN: A Virtual Private Network (VPN) can provide a secure tunnel for all your IoT devices, not just SSH connections.
- TLS/SSL: Transport Layer Security (TLS) and Secure Sockets Layer (SSL) can be used to encrypt data transmitted between IoT devices.
- MQTT: Message Queuing Telemetry Transport (MQTT) is a lightweight protocol designed specifically for IoT devices.
Each of these options has its own strengths and weaknesses, so choose the one that best fits your needs.
Real-World Examples of SSH IoT
Still not convinced? Here are a few real-world examples of how SSH is being used in IoT:
Smart Home Automation
Many smart home systems use SSH to allow users to remotely control their devices. From adjusting the thermostat to turning off the lights, SSH ensures that your home stays secure and connected.
Industrial IoT
In the industrial sector, SSH is used to monitor and manage critical infrastructure, such as power plants and manufacturing equipment. By providing secure remote access, SSH helps companies reduce downtime and improve efficiency.
Conclusion: Your Next Steps
There you have it—the ultimate guide to setting up the best SSH IoT remotely solution for your devices. By following the steps outlined in this article, you can ensure that your IoT devices remain secure, reliable, and easy to manage from anywhere in the world.
So, what’s next? Take action! Set up SSH on your IoT devices, test your connections, and start exploring the possibilities. And don’t forget to share this article with your friends and colleagues. Together, we can make the world of IoT a safer and more connected place.
Got any questions or comments? Drop them below, and let’s keep the conversation going!
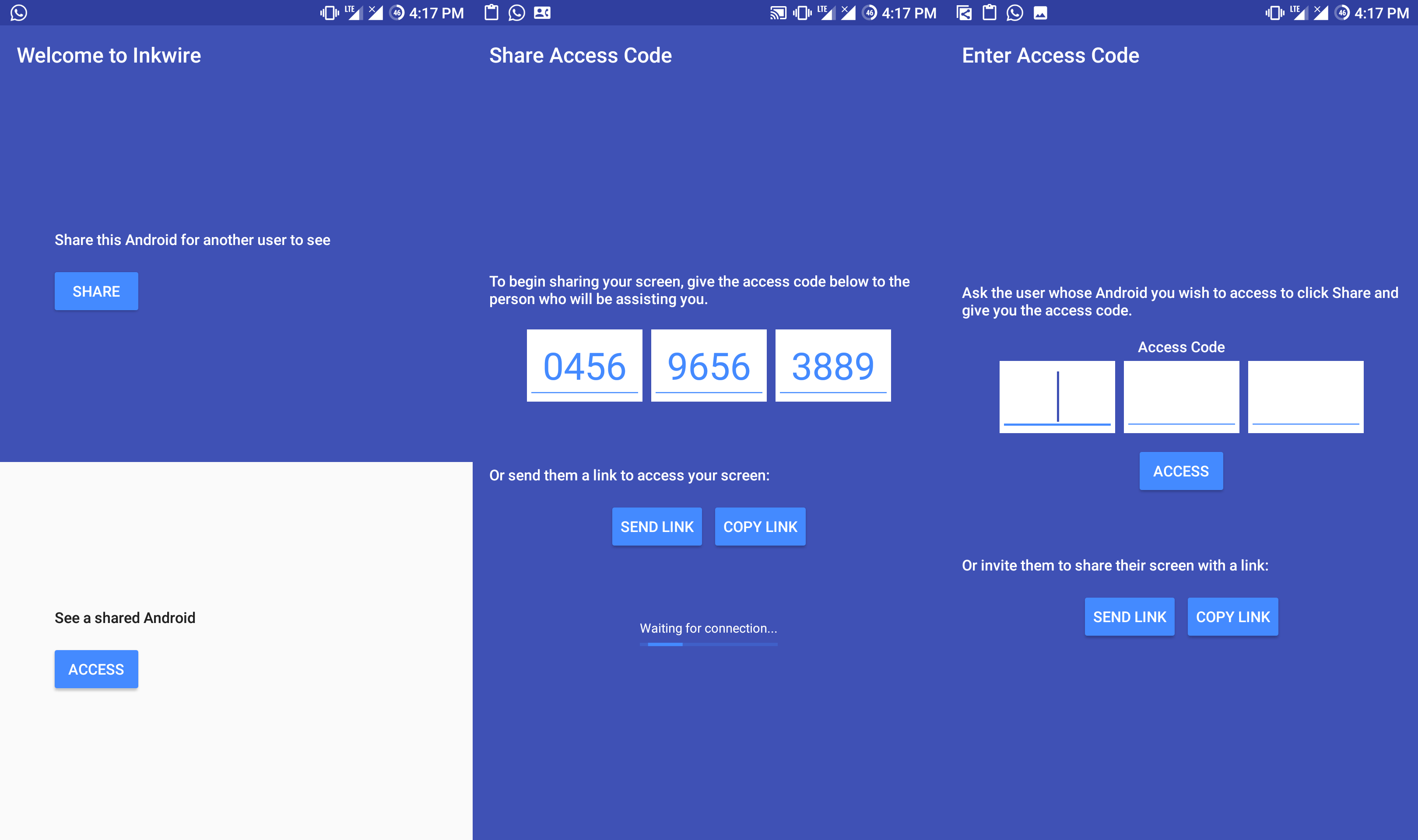


Detail Author:
- Name : Alessia O'Conner
- Username : williamson.leola
- Email : marge.shanahan@hotmail.com
- Birthdate : 1998-04-27
- Address : 98956 Diana Passage Fernandoport, CA 96559
- Phone : 1-430-462-5458
- Company : Ritchie PLC
- Job : Metal Worker
- Bio : Voluptates laudantium quisquam quia maxime reprehenderit enim. Velit incidunt dolorem fugit non architecto itaque. Sunt laborum tenetur totam molestiae quisquam atque occaecati quibusdam.
Socials
twitter:
- url : https://twitter.com/otho.goyette
- username : otho.goyette
- bio : Et placeat esse voluptas expedita ipsa quod. Veniam dolores et vel qui ut non. Dicta nihil quisquam minus numquam esse.
- followers : 4043
- following : 1755
linkedin:
- url : https://linkedin.com/in/othogoyette
- username : othogoyette
- bio : Excepturi aut ut fugiat qui.
- followers : 3150
- following : 716
instagram:
- url : https://instagram.com/otho_goyette
- username : otho_goyette
- bio : Earum omnis sapiente voluptate. Incidunt molestiae odit dolor eos. Qui adipisci nobis officiis non.
- followers : 4813
- following : 1172