Best RemoteIoT SSH Key Management: Unlocking Secure And Efficient Practices
Managing SSH keys for remote IoT devices is one of the most critical aspects of securing your infrastructure. Whether you're a tech enthusiast, a small business owner, or a large-scale IoT deployer, understanding how to handle SSH key management can make or break your system's security. In today's world, where cyber threats are lurking around every corner, you can't afford to neglect this crucial element.
Imagine this: you've set up a network of IoT devices that communicate with each other through encrypted channels. Sounds great, right? But what happens when someone gets unauthorized access to your SSH keys? Suddenly, all those devices are vulnerable to attacks, and your entire system could be compromised. That’s why mastering the art of SSH key management is essential for anyone dealing with remote IoT setups.
Now, let’s dive into why SSH key management matters so much. Think about it like this—your SSH keys are like the keys to your house. If someone steals them, they can walk in without breaking a sweat. By learning the best practices for managing these keys, you're not just protecting your data; you're safeguarding your entire business or personal network. Ready to learn more? Let's get started!
- Movie Rulz 2022 Your Ultimate Guide To The Best Films Of The Year
- 5movierulz 2022 Download Your Ultimate Guide To Movie Downloads
What is RemoteIoT SSH Key Management?
So, what exactly is RemoteIoT SSH Key Management? Simply put, it's the process of securely creating, distributing, storing, and revoking SSH keys for devices that operate remotely in an IoT environment. SSH stands for Secure Shell, which is a cryptographic network protocol that allows secure communication between two systems over an unsecured network. For IoT devices, this means ensuring that only authorized users or systems can access and control your devices.
When you're dealing with remote IoT setups, managing SSH keys becomes even more important because these devices are often spread out across different locations. You can't just walk up to them and manually configure their settings. Instead, you need a robust system in place that can handle all aspects of SSH key management efficiently and securely.
Here’s a quick rundown of what RemoteIoT SSH Key Management involves:
- Movierulz 2024 Telugu Movie Your Ultimate Guide To Streaming Blockbuster Films
- Hdhub4u Movies Your Ultimate Destination For Blockbuster Entertainment
- Generating strong SSH keys
- Distributing keys to authorized devices
- Storing keys securely
- Monitoring key usage
- Revoking compromised keys
Why is SSH Key Management Important for RemoteIoT?
SSH key management is more than just a technical necessity—it's a lifeline for your IoT infrastructure. Without proper management, you're leaving your system wide open to potential threats. Here's why it matters so much:
First off, SSH keys provide a secure way to authenticate users and devices without relying on passwords. Passwords can be easily guessed or stolen, but SSH keys are much harder to compromise. By using SSH keys, you're adding an extra layer of security to your remote IoT devices.
Secondly, managing SSH keys helps you maintain control over who has access to your devices. You can easily revoke access for specific keys if needed, ensuring that only authorized users or systems can interact with your IoT network.
Lastly, having a well-structured SSH key management system in place can save you a ton of time and effort. Instead of manually configuring each device, you can automate the process and focus on more important tasks.
Best Practices for RemoteIoT SSH Key Management
Now that you know why SSH key management is crucial, let's talk about the best practices you should follow to ensure your system stays secure. Here are some tips that will help you get started:
1. Use Strong SSH Keys
One of the most important things you can do is generate strong SSH keys. Weak keys are easier to crack, so it's essential to use algorithms like RSA or ECDSA with sufficient key lengths. For RSA, aim for at least 2048 bits, but 4096 bits is even better if you want maximum security.
2. Limit Access
Not everyone needs access to your IoT devices. Implement strict access controls to ensure that only the right people or systems can use your SSH keys. This might involve setting up role-based access control (RBAC) or using tools like SSH certificates to manage access more effectively.
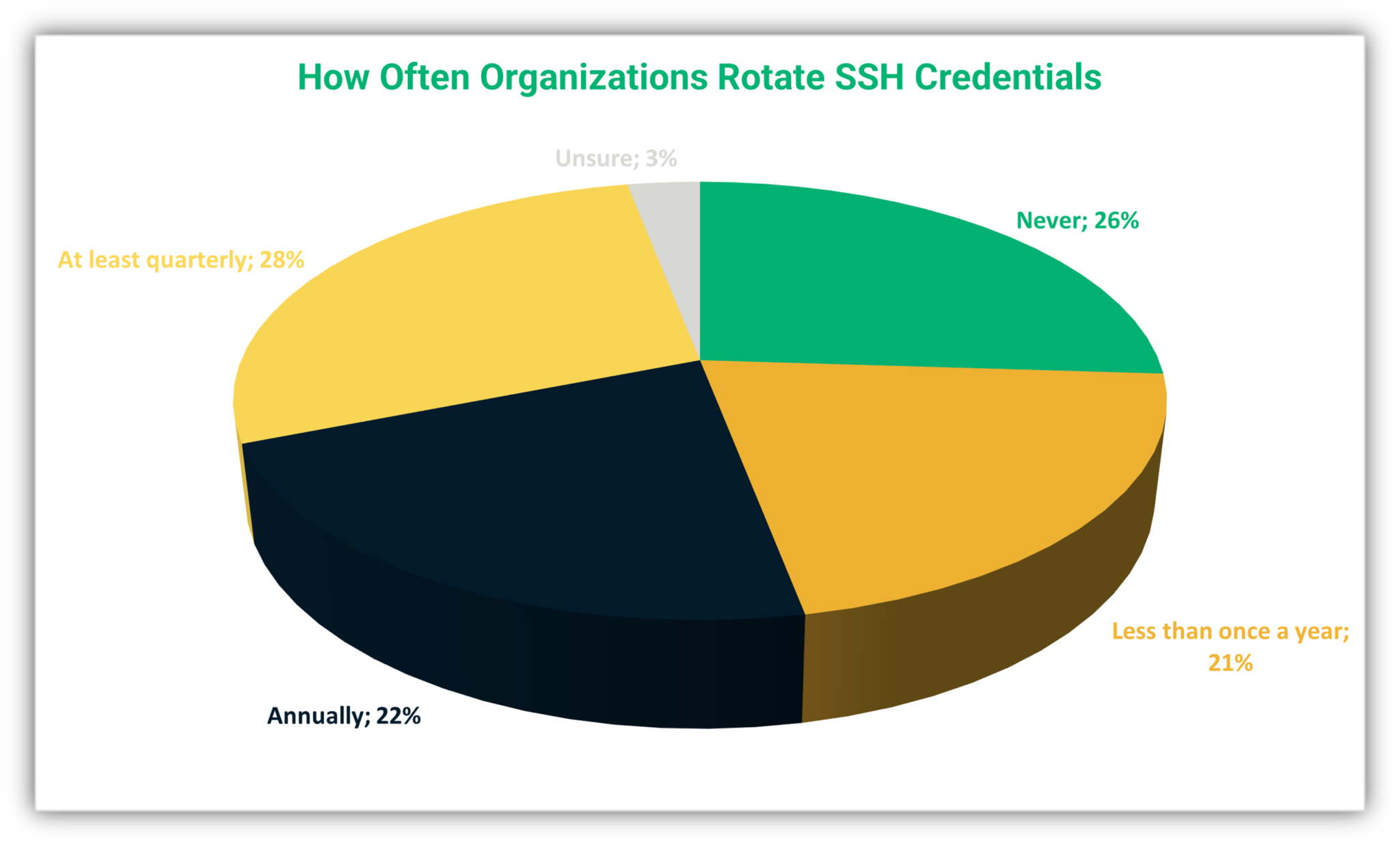
3. Regularly Rotate Keys
Just like you change your passwords every few months, you should also rotate your SSH keys periodically. This reduces the risk of a compromised key being used to access your system. Set up automated processes to handle key rotation, so you don't have to worry about forgetting to do it manually.
4. Monitor Key Usage
Keep an eye on how your SSH keys are being used. If you notice any suspicious activity, such as unauthorized access attempts or unusual login patterns, investigate immediately. Tools like logging and monitoring systems can help you keep track of key usage and detect potential threats early on.
5. Store Keys Securely
Where you store your SSH keys is just as important as how you use them. Never leave private keys lying around in plain text files or unsecured locations. Use encrypted storage solutions or hardware security modules (HSMs) to protect your keys from unauthorized access.
Common Mistakes in SSH Key Management
Even with the best intentions, people often make mistakes when managing SSH keys. Here are some common pitfalls to avoid:
- Using weak or default keys
- Not rotating keys regularly
- Storing keys in insecure locations
- Granting unnecessary access to keys
- Failing to monitor key usage
By being aware of these mistakes, you can take proactive steps to prevent them from happening in your own setup. Remember, the goal is to create a secure and efficient SSH key management system that minimizes risks and maximizes protection.
Tools for Efficient SSH Key Management
Thankfully, there are plenty of tools available to help you manage SSH keys more effectively. Here are a few popular options:
1. SSH Key Management Platforms
Platforms like HashiCorp Vault or CyberArk offer comprehensive solutions for managing SSH keys at scale. They provide features like automated key rotation, secure storage, and detailed monitoring capabilities.
2. OpenSSH
OpenSSH is a widely used tool for managing SSH connections. While it may not have all the bells and whistles of commercial platforms, it's still a powerful option for smaller setups or those on a budget.
3. SSH Certificates
SSH certificates are a great way to simplify key management. Instead of managing individual keys, you can issue certificates that are tied to specific users or devices. This reduces the administrative burden and makes it easier to revoke access when needed.
Challenges in RemoteIoT SSH Key Management
While SSH key management offers many benefits, it's not without its challenges. Here are some of the biggest obstacles you might face:
One major challenge is scalability. As your IoT network grows, managing SSH keys for hundreds or even thousands of devices can become overwhelming. This is where automation and centralized management tools come into play.
Another challenge is ensuring compliance with security standards and regulations. Depending on your industry, you may need to adhere to specific guidelines for managing SSH keys. Make sure you're familiar with these requirements and implement measures to meet them.
Future Trends in SSH Key Management
The field of SSH key management is constantly evolving, with new technologies and approaches emerging all the time. Here are a few trends to watch out for:
First, there's a growing emphasis on zero-trust security models. These models assume that no device or user can be trusted by default, requiring continuous verification and authentication. This approach can significantly enhance the security of your SSH key management system.
Another trend is the increased use of artificial intelligence and machine learning for monitoring and analyzing key usage. These technologies can help detect anomalies and potential threats faster than traditional methods, giving you a head start on addressing security issues.
Data and Statistics Supporting SSH Key Management
Let’s take a look at some data that highlights the importance of SSH key management:
- A recent study found that 60% of data breaches involve compromised SSH keys.
- On average, organizations spend $3.86 million dealing with the aftermath of a data breach.
- 90% of IT professionals agree that SSH key management is a critical component of their security strategy.
These numbers paint a clear picture: SSH key management isn’t just important—it’s essential for protecting your business and your data.
Conclusion: Take Action Today
By now, you should have a solid understanding of why SSH key management is so important for your remote IoT devices. From generating strong keys to monitoring usage and storing them securely, every step in the process plays a vital role in keeping your system safe.
So, what’s next? Start implementing the best practices we’ve discussed and explore the tools available to streamline your SSH key management. And don’t forget to stay up-to-date with the latest trends and technologies in this ever-evolving field.
Before you go, we’d love to hear your thoughts. Do you have any tips or tricks for managing SSH keys? Share them in the comments below! And if you found this article helpful, be sure to share it with your friends and colleagues. Together, we can make the IoT world a safer place for everyone.
Table of Contents
- What is RemoteIoT SSH Key Management?
- Why is SSH Key Management Important for RemoteIoT?
- Best Practices for RemoteIoT SSH Key Management
- Common Mistakes in SSH Key Management
- Tools for Efficient SSH Key Management
- Challenges in RemoteIoT SSH Key Management
- Future Trends in SSH Key Management
- Data and Statistics Supporting SSH Key Management
- Conclusion: Take Action Today


Detail Author:
- Name : Nova Johnson
- Username : dejah.dietrich
- Email : tkub@brown.biz
- Birthdate : 1980-10-26
- Address : 28144 Schamberger Path North Elvisport, MA 29651
- Phone : +18547280239
- Company : Moore, Marquardt and Zboncak
- Job : Rehabilitation Counselor
- Bio : Quibusdam ea corporis repellat facere eaque. Itaque commodi voluptatibus excepturi. Aspernatur laborum sit voluptas soluta cum exercitationem.
Socials
tiktok:
- url : https://tiktok.com/@rae_murazik
- username : rae_murazik
- bio : Maxime eum aut voluptatem ipsa quaerat accusamus nobis.
- followers : 6172
- following : 2868
instagram:
- url : https://instagram.com/murazikr
- username : murazikr
- bio : Dolor reprehenderit et dolores beatae quae. Impedit assumenda et eius.
- followers : 6728
- following : 1167
facebook:
- url : https://facebook.com/rae_id
- username : rae_id
- bio : Non reprehenderit consectetur rerum dolor reprehenderit.
- followers : 6746
- following : 947
twitter:
- url : https://twitter.com/murazik1985
- username : murazik1985
- bio : Odio illum ex molestias. Accusamus aut quasi quidem qui. Dolor sit illum ea atque. Et eveniet voluptas rerum provident in.
- followers : 266
- following : 1531
linkedin:
- url : https://linkedin.com/in/murazikr
- username : murazikr
- bio : Et deserunt eum qui eius.
- followers : 1826
- following : 2688